|
 |
|||||||
| ||||||||

 Clarus leads and assists organizations meet federal and/or industry IT security requirements. Recent clients include Department of Education loan servicers and Private Collection Agencies. Clarus clients also include a large national credit rating agency, Not-for-Profit entities, and state government organizations. Our services focus on helping our clients understand, implement and manage these risk framework standards: Clarus leads and assists organizations meet federal and/or industry IT security requirements. Recent clients include Department of Education loan servicers and Private Collection Agencies. Clarus clients also include a large national credit rating agency, Not-for-Profit entities, and state government organizations. Our services focus on helping our clients understand, implement and manage these risk framework standards:Clarus conducts risk framework assessments of organizations, establishing detailed (Project) work plans with accompanying system documentation in support of meeting federal and industry security standards necessary for federal and contract compliance. Clarus works with and assists organizations implement the applicable information security standards and controls, maintain information security compliance, and identify risk vulnerabilities and threats in order to support risk management decisions and protect the information assets of the organization. Clarus has four Information Security focus areas: 1. Information Security Compliance and Assessment Information Security Compliance and Assessment Clarus conducts compliance assessments for organizations to help them understand and manage their information security risk in accordance with their mission, industry classification and standard, applicable government requirements, client contractual requirements, and business objectives. Clarus assessments typically help organizations achieve: Authority to Operate Federal agencies utilize independent assessors like Clarus to review and evaluate an organizations control framework, vulnerabilities, security documentation and plans, and management of the systems, facilities, and personnel to determine if they meet FISMA/NIST standards. Clarus conducts pre-assessments to help organizations understand potential gaps in their security policies, processes and procedures so that they may begin to mitigate those findings or vulnerabilities before a formal assessment is completed. Working in conjunction with our client subject matter experts, we develop a comprehensive road map of the tasks and activities which should be completed before a formal assessment is initiated. Clarus performs independent assessment services in accordance with federal policies and standards, NIST publication guidelines for system operating environments, physical and personnel security, and IT infrastructure management. We evaluate the extensive documentation that is required by federal agencies before they authorize their assets to be placed on contractor systems, ensuring that IT Security controls, policies, processes, and procedures are in accordance with federal agency standards. Industry Certification Assessments Clarus provides security risk assessment services based on FFIEC and HIPAA requirements and the ISO/IEC-27001 framework. Our risk assessments identify and help our clients understand their risks to the confidentiality, integrity, and availability of information and information systems, applying and assessing the specific controls needed to meet industry defining standards. We understand and recognize the critical nature, sensitivity, and data information protection requirements within these specific requirements, the laws which must be adhered to protect customers and information assets, and the ongoing need to proactively monitor and protect the systems and processes in place to achieve customer confidence. Clarus risk assessments consist of the identification and analysis of organizational assets in relation to potential threats and vulnerabilities, resulting in a ranking of risks to mitigate. The assessment results in information used to develop strategies to mitigate those risks. Clarus delivers customized and agreed-upon assessment services based on individual agency and organization need, and where the organization believes it resides on the security continuum. Information Security Continuous Monitoring Clarus provides Information Security Continuous Monitoring (ISCM) services to commercial organizations. Clarus utilizes a robust ISCM program to help organizations move from compliance-driven risk management to data-driven risk management. We provide the organization with information necessary to support risk response decisions, security status information, and ongoing insight into security control effectiveness. The Clarus approach uses the following steps: The question of how often to assess each control as part of an ISCM program is possibly the most important consideration. Clarus utilizes a combination of inputs including the method of review (automated and manual) and combines it with the criticality and volatility of the application to determine the frequency of the control review. Input factors, as shown in the chart below, are derived from NIST SP 800-137 and OMB A-130 publications. 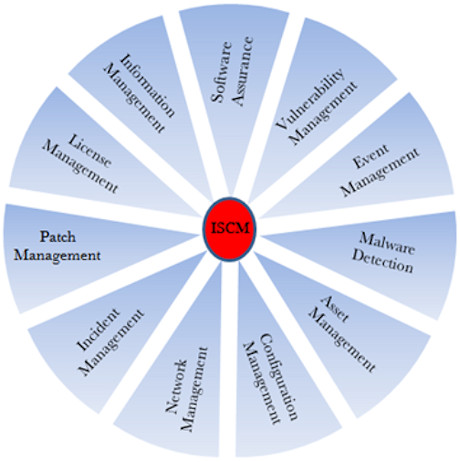 Program Development and Management Clarus helps organizations propose, develop, construct, coordinate, and implement information security policies, controls, standards, and procedures. By working with key IT and security resources, data owners, and governance groups, policies and the necessary corresponding security structure is developed. Clarus helps ensure that an organizations policies support compliance with external requirements, and are properly disseminated and communicated to all staff, including communicating individual responsibilities. Clarus establishes a framework where systems, processes, and people are monitored to help ensure vulnerabilities are appropriately identified and mitigated. We develop and implement ongoing risk assessment programs targeting information security and privacy matters, recommend methods for vulnerability detection and remediation, and oversee vulnerability testing. Information Security Operations Clarus assists organizations implement and manage the Enterprise Security Office. Clarus has supported client organizations create an overall strategy and implementation plan for corporate-wide security functions associated with information technology applications, communications, data center, and the physical security, protection, and privacy of the organization and employees. Clarus performs the following activities: |
 Have a question about the information on this page or any of our other services? Feel free to email us.
Have a question about the information on this page or any of our other services? Feel free to email us.
Our Clients Include
|

|
 Service Areas
Service Areas